4 minutes
Steps to set-up Yubikey authentication to FreeIPA
This post presents happy path (or reference architecture). The aim is to provide reproducible steps to configure functioning smart card environment.
There are multiple ways to set-up smart card authentication. Configuration varies based on factors like
- the CA that signs keys on smart cards
- properties of CN (Common Name) that are required
- identity mapping rules (how to translate CN from smart card to identity)
- versions of client & server stack
This blog post gives concrete steps on how to set-up FreeIPA 4.6.6 (Red Hat Identity Management) server for authentication with yubikey smart card.
Generate private key and CSR inside yubikey
First thing we need is to generate public/private key pair on the smart card. The public part will then be signed by FreeIPA CA and hence we need to generate CSR (Certificate Signing Request) along the way.
The easiest and the most approachable way to generate CSR using GUI manager yubikey-manager-qt. Although there are other ways to achieve this using either yubico-piv-tool, pkcs11-tool, or p11tool
Installing YubiKey Manager
Installation of the Yubikey manager is very easy and straight forward. Since we need this program only for initial settings. We can use latest AppImage from their release page.
wget https://developers.yubico.com/yubikey-manager-qt/Releases/yubikey-manager-qt-1.1.3-linux.AppImage
chmod u+x yubikey-manager-qt-1.1.3-linux.AppImage
./yubikey-manager-qt-1.1.3-linux.AppImage
Generate CSR
Insert Yubikey and navigate to PIV application in the YubiKey Manager.
Go to Certificates and hit Generate button.
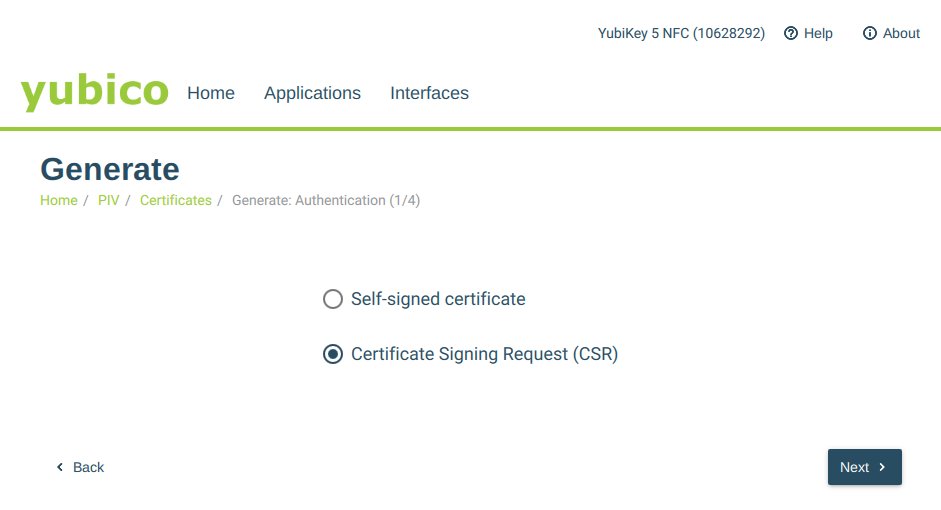
Select Certificate Signing Request (CSR) option. This will generate private key on the card (that never leaves the card) and CSR that you can store in the computer.
Pick Subject Name for your CSR. It may turn out preferential to choose the same name as your login to the FreeIPA.
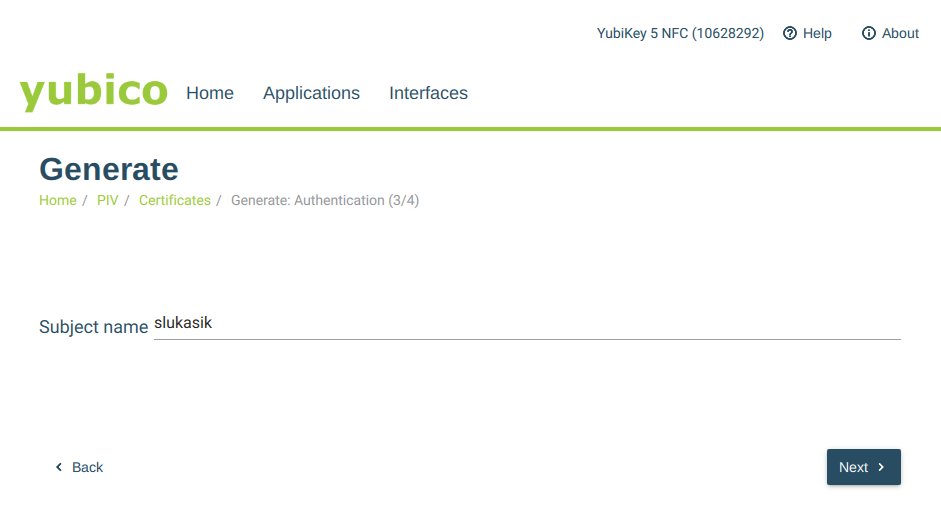
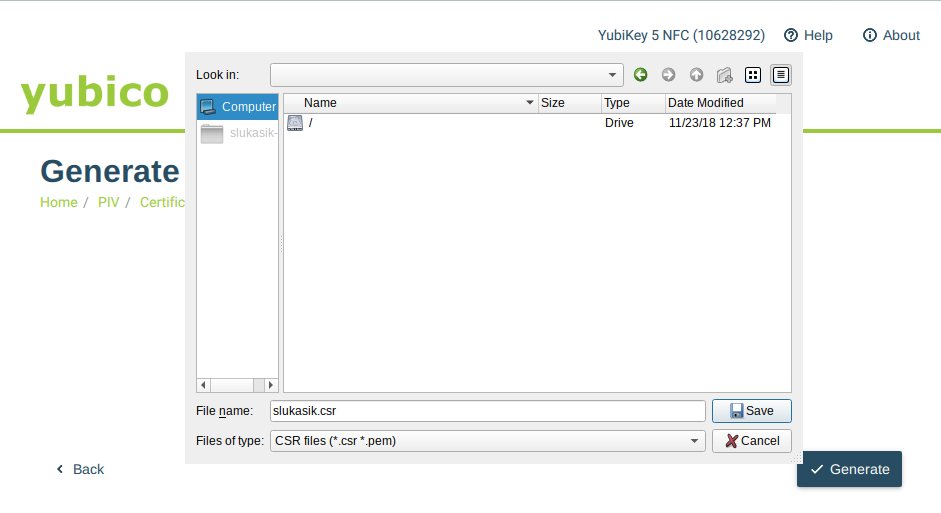
Don’t forgot to store CSR on the computer. You will later need this CSR to be signed by FreeIPA server CA.
Set-up FreeIPA server
Setting is very easy and straight forward. You can either consult Red Hat Indentity Management Documentation for detailed description. Nevertheless, following commands run on freeipa server will set you up.
kinit admin
ipa-advise config-server-for-smart-card-auth > config-server-for-smart-card-auth.sh
chmod u+x config-server-for-smart-card-auth.sh
./config-server-for-smart-card-auth.sh ca.crt.pem
Sign Your CSR by FreeIPA
Log in to the webui as admin user.
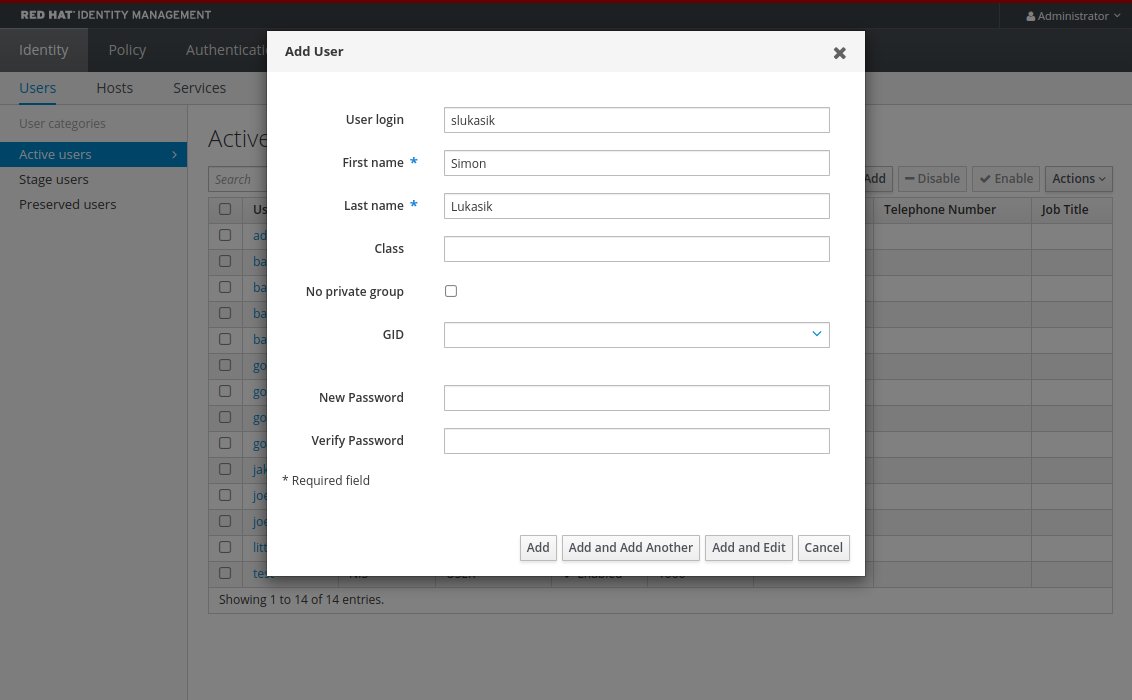
Create user used for the authentication (unless already exists)
Add new certificate for that user.
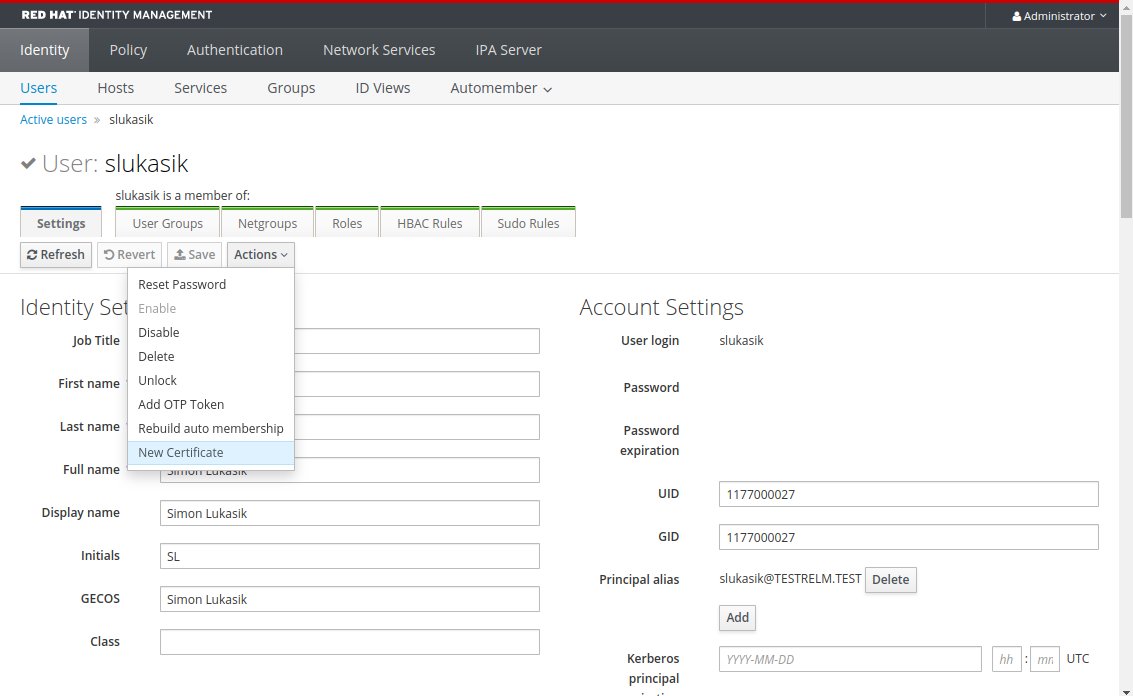
Pass in content of the CSR file you created in previous step.

Server will sign the CSR and asign resulting certificate to the user.
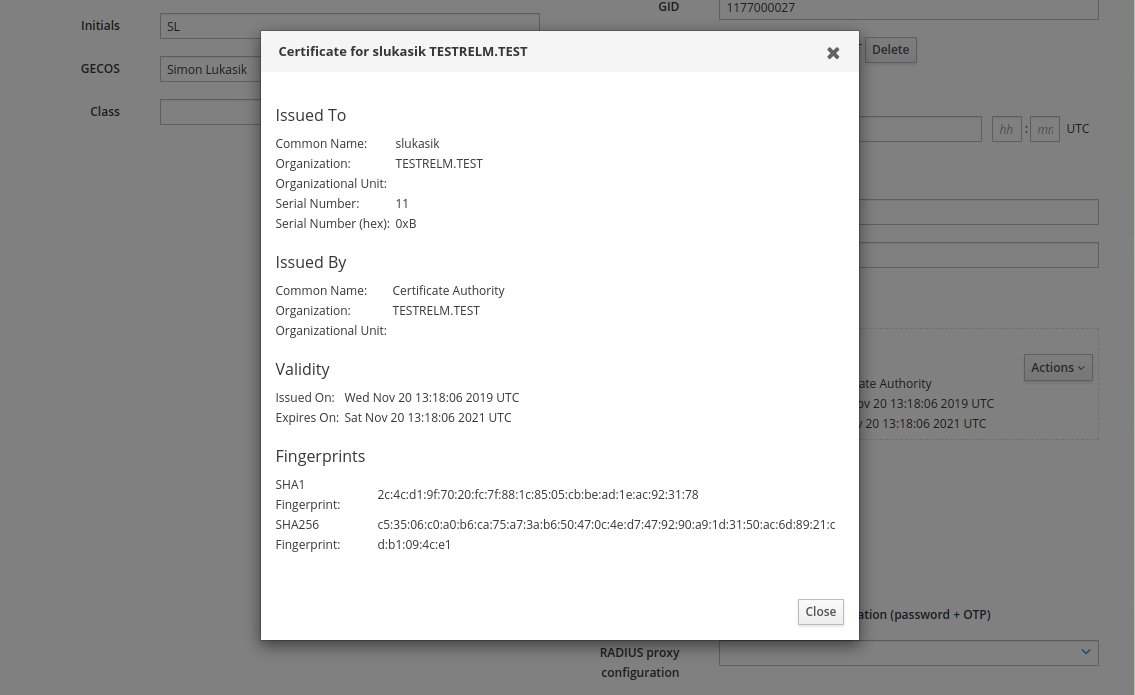
Download the user certificate. This is the certificate for the private key you generated on the smart card in previous steps.
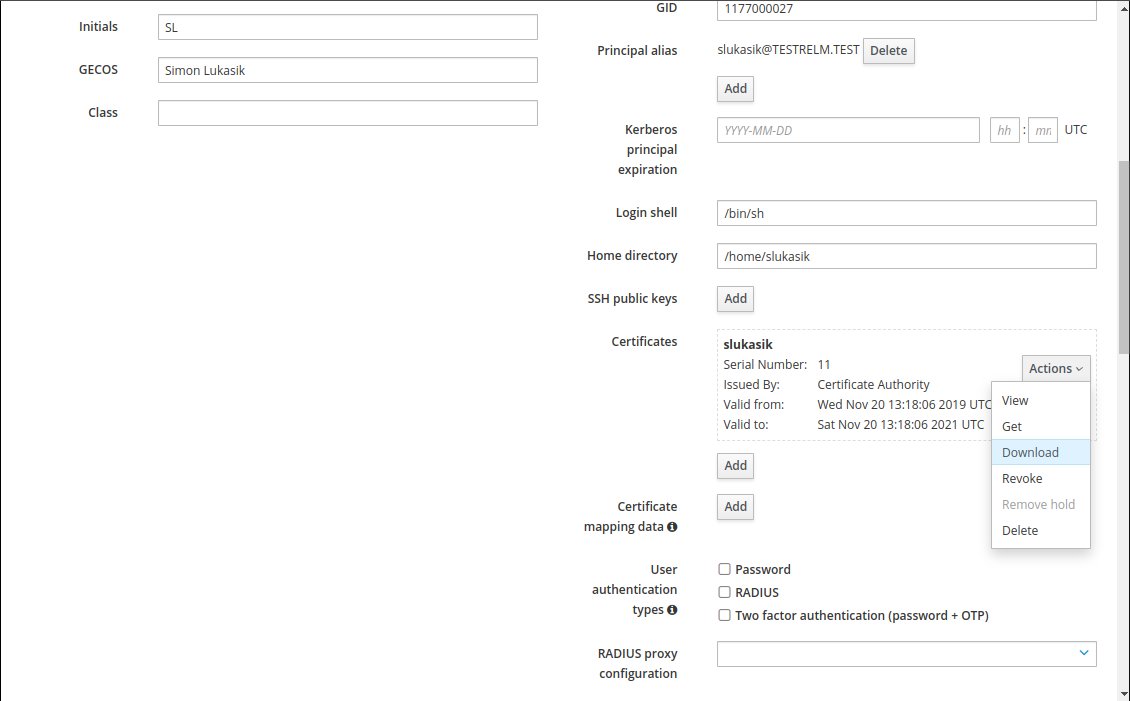
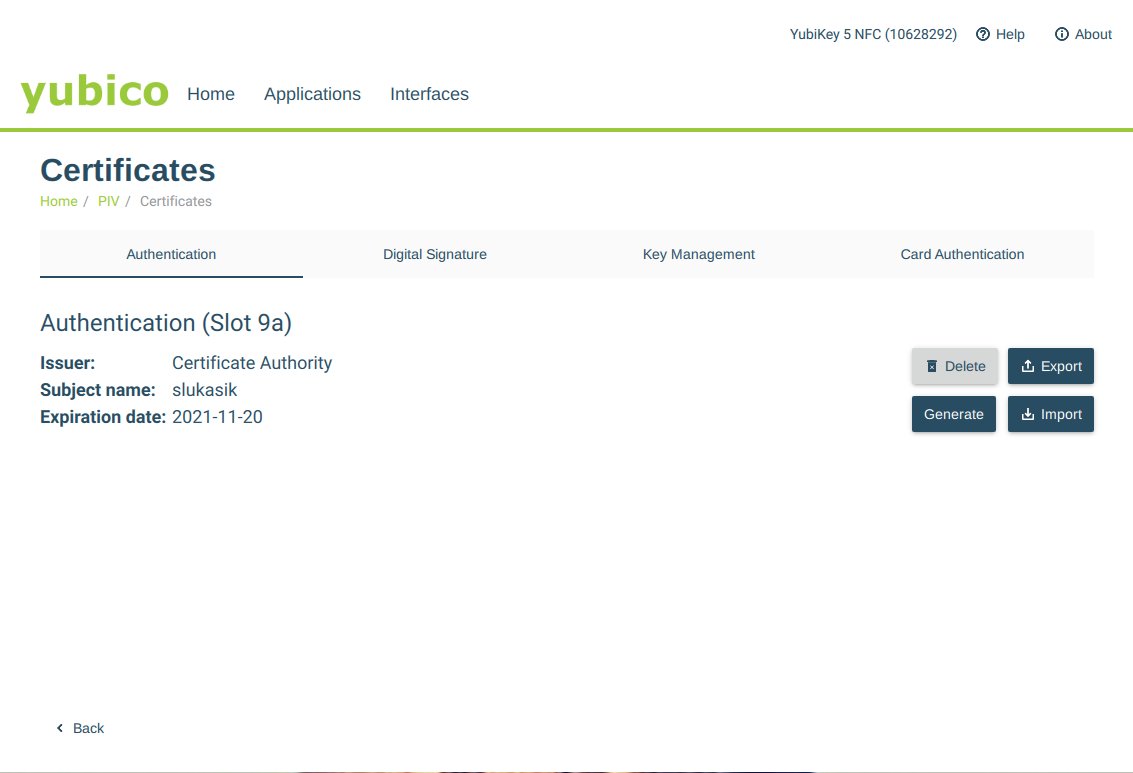
Import Signed Certificate back to the smart card
Choose the same authentication slot that contains the private key.
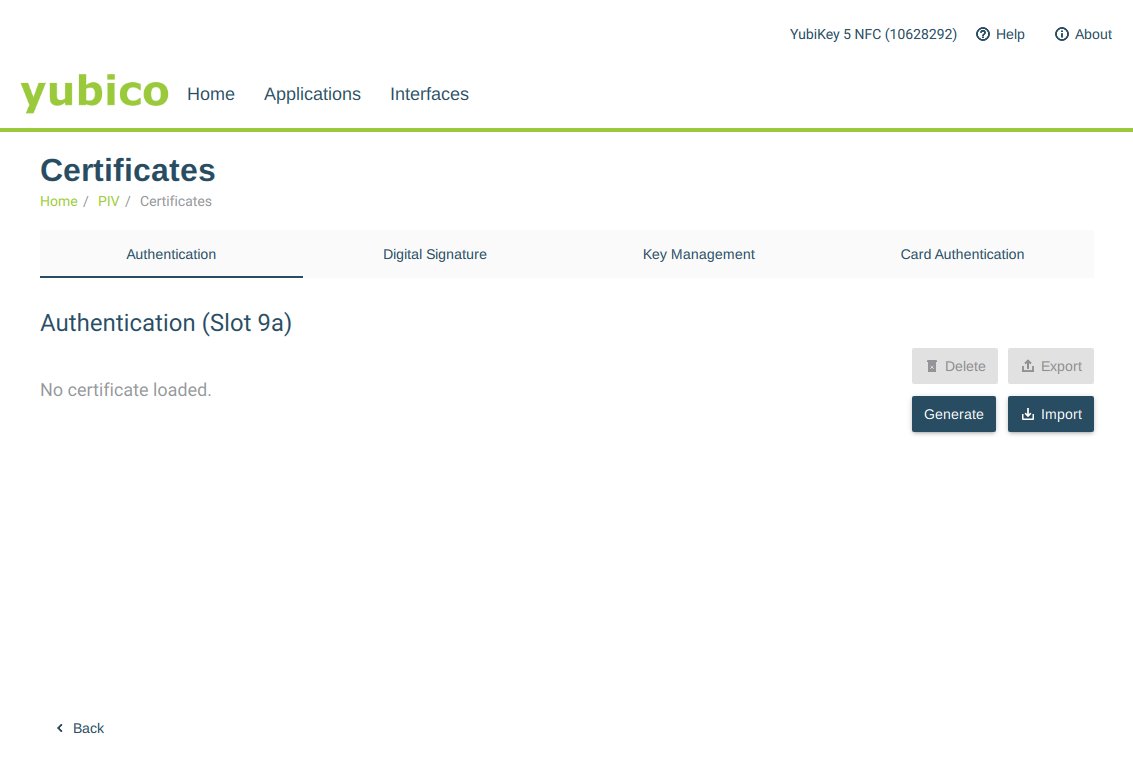
Import the certificate that was signed by identity server previously.
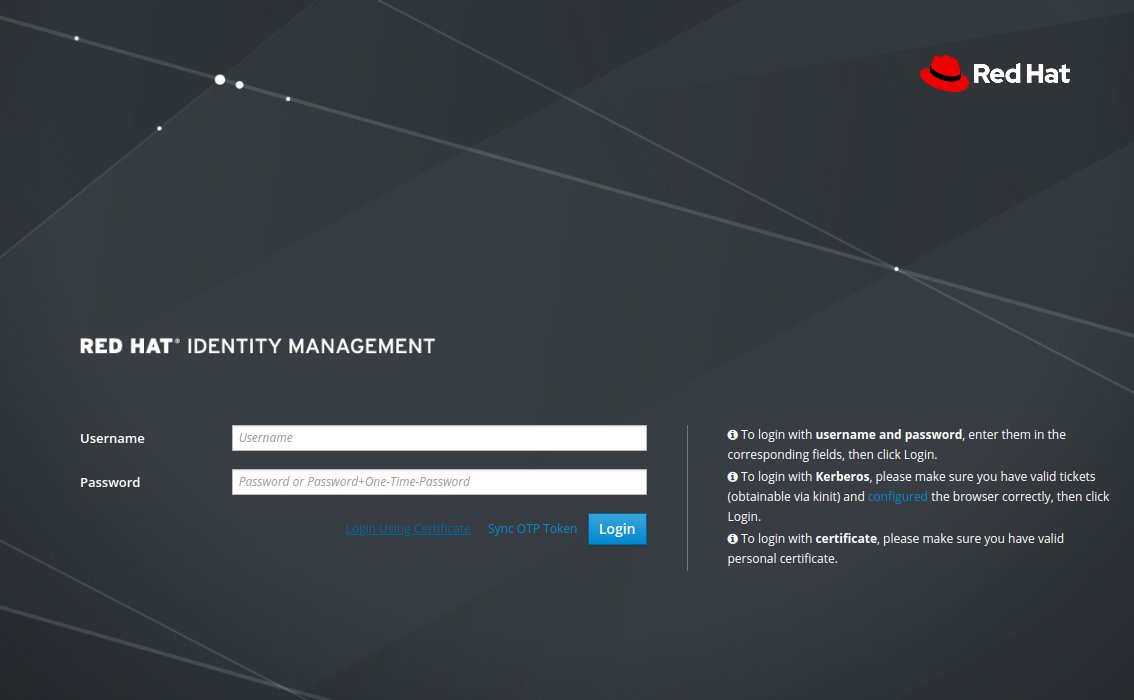
Try logging in
Instead of typing up the login and password, click the blue button Login Using Certificate.
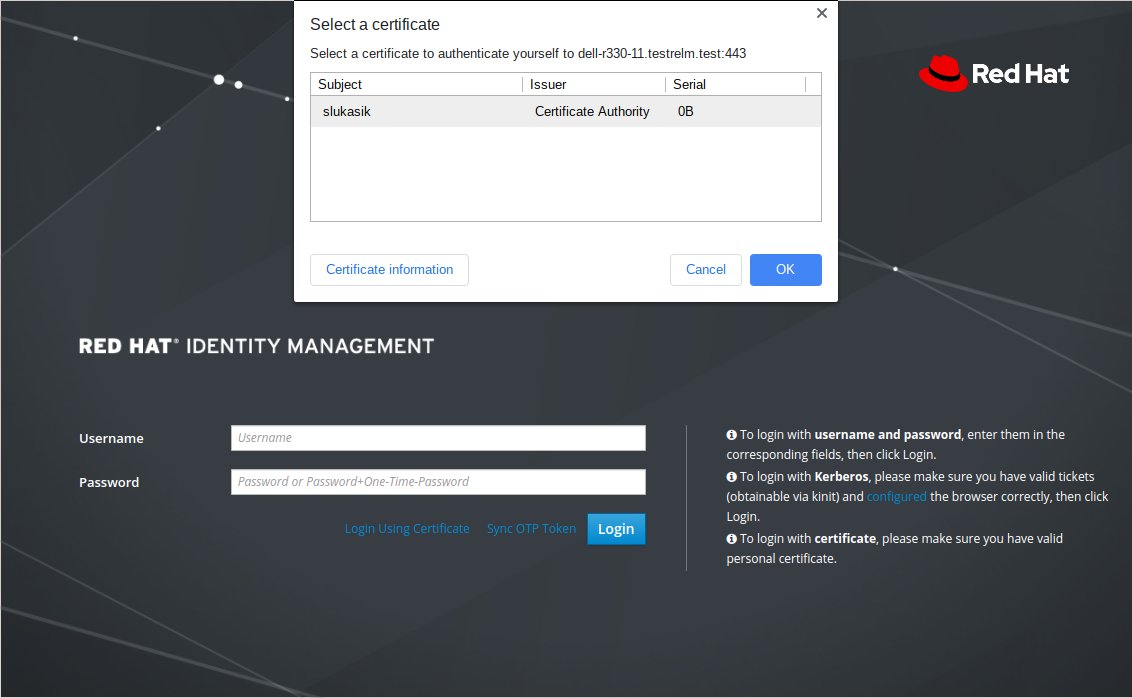
Pin entry dialog should show up asking you for the smart card pin. In case you don’t see pin entry dialog learn how to diagnose your client system.

Next dialog that shows up lets you choose certificate to be used for authentication. Since we have only one certificate on the Yubikey only one shows up here.
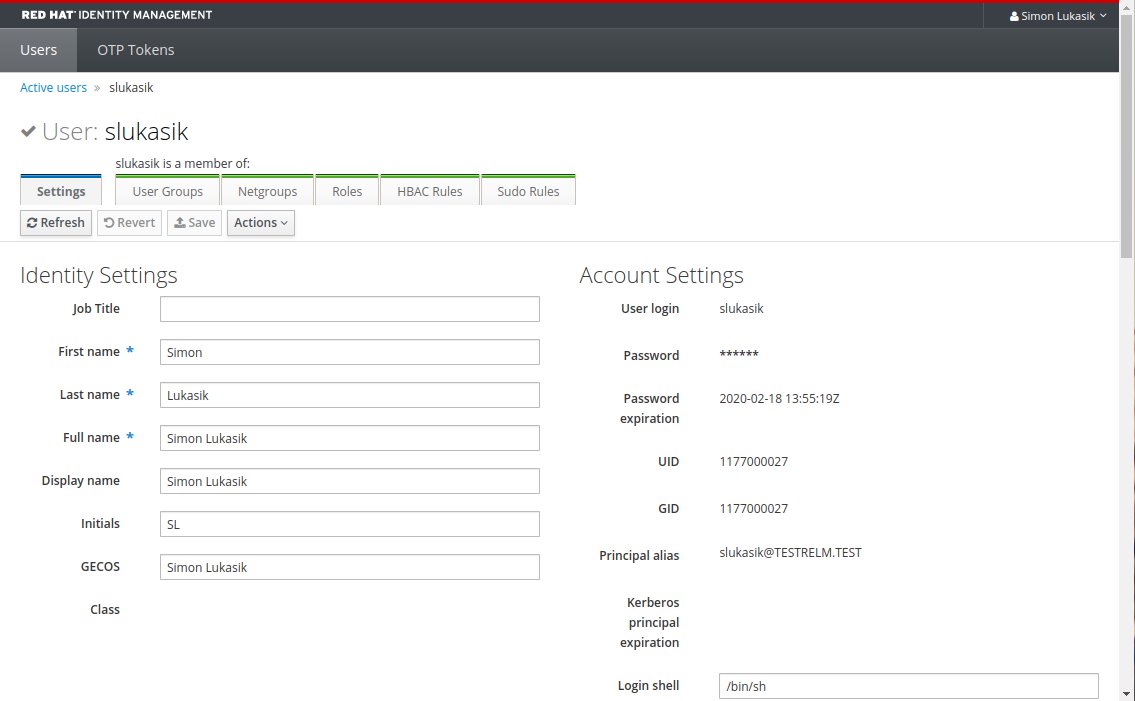
Voilà!

For some reason the authentication failed for me on first try. This may happen to You as well as there is about dozen of components that needs to play in orchestra. Let’s see if I can debug my failure.
Debug and fix the failure
If you get stuck, I suggest to visit comprehensive collection of debugging hints written by Florence Blanc-Renaud. Although, in my particular case, I have got different type of problem.
I have started debugging with apache error logs. I tailed the logs and re-authenticate, to see the failure in the real-time.
tail -f /var/log/httpd/*
==> /var/log/httpd/error_log <==
[Wed Nov 20 14:44:18.041621 2019] [lookup_identity:error] [pid 19766] [client 10.40.204.110:58298] lookup_user_by_certificate failed [dbus_connection_send_with_reply_and_block(org.freedesktop.sssd.infopipe.Users.FindByNameAndCertificate)]: [Permission denied], referer: https://dell-r330-11.testrelm.test/ipa/ui/
[Wed Nov 20 14:44:18.041637 2019] [lookup_identity:error] [pid 19766] [client 10.40.204.110:58298] lookup_user_by_certificate cleared r->user, referer: https://dell-r330-11.testrelm.test/ipa/ui/
[Wed Nov 20 14:44:18.041660 2019] [core:error] [pid 19766] [client 10.40.204.110:58298] AH00027: No authentication done but request not allowed without authentication for /ipa/session/login_x509. Authentication not configured?, referer: https://dell-r330-11.testrelm.test/ipa/ui/
It seems that for some reason mod_lookup_identity is getting permission denied when accessing D-Bus call. D-Bus calls can be authenticated, so my first idea was to investigate whether mod_lookup_identity (apache process, apache user) can access the org.freedesktop.sssd.infopipe.Users.FindByNameAndCertificate.
Looking into the /etc/sssd/sssd.conf, I can see the following lines:
[ifp]
allowed_uids = ipaapi, root
It seems that only ipaapi and users are allowed to access the api. Let’s add apache user to the list.
[ifp]
allowed_uids = ipaapi, root, apache
restart sssd
systemctl restart sssd.service
and return back to web authentication:



Voilà!
Kudos go to Jan Pazdziora who discussed the set-up with me several times. Thank You Adelton!